Are you eager to land a SOC Analyst job but feeling overwhelmed by the abundance of information?
Yes, but with certifications, hands-on experience, and focus, you can confidently secure a SOC Analyst job.
Tell you something interesting: According to (ISC)², the cybersecurity workforce gap is currently at 3.4 million professionals globally. That’s precisely why SOC Analyst positions are in such high demand.
I remember when I first started exploring cybersecurity careers in 2015 — the sheer amount of information was daunting!
Over the past decade, I’ve helped many professionals transition from complete beginners to successful SOC analysts.
This guide equips you with everything you need to launch your SOC Analyst career, from essential skills and certifications to salary expectations and industry insights.
Take advantage of this opportunity to enter one of the most critical and rewarding fields in cybersecurity.
See also: Additional Resources for Cybersecurity Beginners
Let’s start! Introduction to SOC Analysis and Its Role in Network Logs.
What is a SOC Analyst Job?

Based on my years of experience working in security operations centers, let me explain what a SOC Analyst does.
A SOC Analyst job is like a digital detective and first responder career.
Think of it as the guardians of an organization’s digital assets job — that watch for suspicious activity 24/7.
Here’s what the role typically involves:
- Monitoring security alerts and network traffic in real-time
- Investigating potential security incidents using various tools
- Responding to and documenting security breaches
- Maintaining security tools and systems
- Collaborating with other IT teams for incident response
I still remember my first “real” security incident — a ransomware attempt that I caught at 3 AM during a night shift!
Trust me, the adrenaline rush of detecting and stopping cyber threats never gets old.
SOC analyst Job Responsibilities

In the fast-evolving cybersecurity field, understanding a SOC Analyst job core responsibilities is crucial for success.
SOC Analysts are the digital front-line defenders tasked with safeguarding organizational assets against cyber threats.
Key Responsibilities Include of a SOC Analyst job:
Monitoring and analyzing security alerts from SIEM platforms:
SOC Analysts use Security Information and Event Management (SIEM) tools to detect unusual or suspicious activity in real-time across networks and systems.
Investigating and documenting security incidents:
Analysts review alerts to assess whether they indicate real threats. They record their conclusions and create comprehensive reports for resolution and future reference.
Performing threat analysis and proactive threat hunting:
Beyond reacting to alerts, SOC Analysts proactively search for potential vulnerabilities or threats that may not have triggered an alarm.
Collaborating with IT teams to strengthen security measures:
SOC Analysts work closely with IT staff to improve security protocols, patch vulnerabilities, and ensure systems remain robust against attacks.
Maintaining and updating security tools and protocols:
Analysts ensure tools like firewalls, antivirus software, and SIEM systems are up-to-date and configured correctly to protect against evolving threats.
Important Elements:
- Current industry statistics: SOC Analysts jobs are integral to combating a 3.4 million global cybersecurity workforce gap.
- Day-in-the-life examples: A SOC Analyst’s shift may include handling a simulated phishing attack to train employees.
- Real job description analysis: Highlighting responsibilities such as malware analysis and compliance reporting.
Entry-Level SOC Analyst Job Requirements

Want to know what it takes to land your first SOC Analyst job role?
Based on my experience hiring junior analysts, here’s what you need:
Education Role of a SOC Analyst Job:
- Bachelor’s degree in Cybersecurity, IT, or a related field (though not always mandatory)
- Relevant certifications like Security+, Certified in Cybersecurity (CC), or GSEC
- Basic networking knowledge (TCP/IP, OSI model)
Technical Skills of a SOC Analyst Job:
Understanding of common security tools (SIEM, IDS/IPS):
Knowledge of SIEM (Security Information and Event Management) tools like Splunk or IBM QRadar helps SOC Analysts job detect and manage security threats. IDS/IPS (Intrusion Detection/Prevention Systems) are used to monitor and block malicious activity in networks.
Basic scripting abilities (Python or PowerShell) of a SOC Analyst Job:
Scripting skills enable analysts to automate repetitive tasks, analyze logs, and develop custom scripts for investigating and mitigating threats efficiently.
Knowledge of common attack vectors and vulnerabilities of a SOC Analyst Job:
Familiarity with attack methods (e.g., phishing, ransomware) and system vulnerabilities helps analysts quickly identify and respond to threats.
Familiarity with Windows and Linux operating systems of a SOC Analyst Job:
Understanding these operating systems allows SOC Analysts to navigate, secure, and investigate incidents across diverse IT environments. Soft Skills:
- Strong analytical thinking
- Excellent communication abilities
- Team collaboration
- Attention to detail
- Ability to work under pressure
Trust me, most employers value attitude and willingness to learn over perfect technical knowledge for entry-level positions.
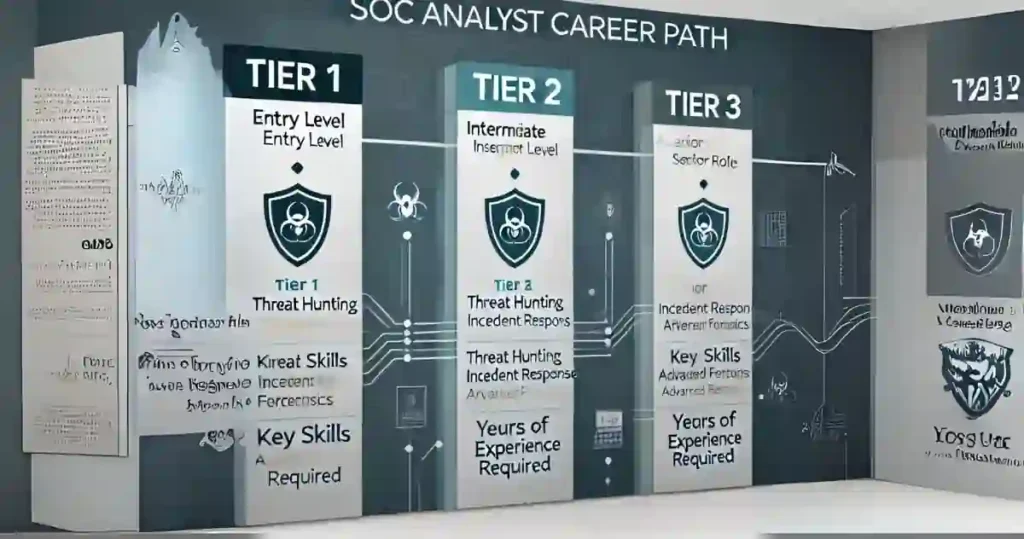
SOC Analyst Job Progression
Let me share how the typical SOC Analyst job path looks, based on my journey and those I’ve mentored:
Tier 1 SOC Analyst Job (Entry Level):
- Focus on alert monitoring and triage
- 0-2 years experience
- Salary range: $50,000 – $75,000
- Key skills: Basic security tools, alert monitoring
Tier 2 SOC Analyst Job (Intermediate):
- Deep dive investigations
- 2-5 years experience
- Salary range: $75,000 – $95,000
- Key skills: Threat hunting, incident response
Tier 3 SOC Analyst Job (Senior):
- Advanced threat hunting and incident response
- 5+ years experience
- Salary range: $95,000 – $130,000
- Key skills: Advanced forensics, team leadership
Specific Salary Ranges by Region of a SOC Analyst Job:
- United States: Average $85,000
- Europe: Average $70,000
- Asia-Pacific: Average $65,000
Beyond Senior Level of a SOC Analyst Job:
- SOC Manager
- Security Architect
- Threat Intelligence Specialist
- Incident Response Manager
Important Elements of a SOC Analyst Job:
- Growing interest in remote positions: Salaries for remote SOC roles often vary but remain competitive globally, with U.S. remote analysts earning an average of $85,000 annually and flexible global roles seeing steady growth.
- Encouraging but realistic tone: While salaries are promising, regional disparities—such as higher U.S. pay compared to Asia-Pacific—and skill gaps, like advanced threat-hunting proficiency, impact earning potential.
Essential Tools and Technologies of a SOC Analyst Job
Throughout my career, I’ve used countless security tools. Here are the most crucial ones you need to master:
SIEM Platforms of a SOC Analyst Job:
Splunk for SOC Analyst Job: A popular SIEM tool that collects, indexes, and analyzes machine-generated data in real-time to detect security threats.
IBM QRadar: Provides comprehensive threat detection by correlating logs and flow data for network security monitoring.
Exabeam: Uses advanced analytics to detect insider threats and automate incident response.
Microsoft Sentinel: A cloud-native SIEM solution integrated with Azure for scalable threat detection and response.
Network Monitoring for a SOC Analyst Job:
Wireshark: A packet analyzer tool that captures and analyzes network traffic in real-time for troubleshooting and security.
Snort: An open-source intrusion detection and prevention system that analyzes traffic for suspicious patterns.
Zeek (formerly Bro): A robust network analysis framework that provides in-depth monitoring and logging of network traffic.
Endpoint Security for a SOC Analyst Job:
Carbon Black: Protects endpoints by monitoring activities and blocking malicious behaviors with real-time response capabilities.
CrowdStrike: Offers cloud-based endpoint protection with AI-driven threat detection and incident response.
Microsoft Defender ATP: Provides integrated threat detection and response for Windows environments to protect endpoints.
Threat Intelligence for a SOC Analyst Job:
AlienVault OTX: A threat intelligence platform where users share and access information on emerging threats.
VirusTotal: A free service aggregating data from multiple antivirus engines to analyze suspicious files and URLs.
MISP: A collaborative threat intelligence platform that helps organizations share threat data for better security coordination.
Required Certifications and Skills of a SOC Analyst Job
Building a robust skill set and earning the proper certifications are key to succeeding in this field.
Certification Roadmap:
- Entry-Level: CompTIA Security+, EC-Council CSA
- Intermediate: CISSP, GCIH
- Advanced: OSCP, GCFA
Skills Progression Timeline:
- Mastering SIEM tools (Splunk, QRadar) in the first year.
- Gaining proficiency in scripting languages (Python, PowerShell) within three years.
- Developing advanced forensic and incident response skills by year five.
Important Elements:
- Increasing demand for cloud security skills: Skills in cloud platforms like AWS and Azure are highly valued.
- Clear, actionable advice: Focus on certifications that align with desired job levels.
Real Career Progression Examples of a SOC Analyst Job
A clear roadmap of career advancement helps to aspire SOC Analysts visualize their future.
Career Progression Path:
1. Tier 1 (Entry-Level):
Entry-level SOC Analysts focus on monitoring security alerts and performing basic triage to determine their severity. This role serves as the first line of defense in identifying potential incidents.
2. Tier 2 (Intermediate):
Analysts at this level dive deeper into investigations and handle more complex security incidents. They specialize in incident response, threat analysis, and providing insights to mitigate future risks.
3. Tier 3 (Senior-Level):
Senior analysts lead advanced threat-hunting efforts, manage high-level incident responses, and mentor junior team members. They also contribute to strategic decisions on security improvements.
4. Beyond Senior Level:
Professionals move into specialized roles such as SOC Manager (overseeing operations), Security Architect (designing security frameworks), or Threat Intelligence Specialist (analyzing threat trends to anticipate risks). These roles often involve leadership and strategic planning. Important Elements:
- Real job descriptions analysis: Highlighting real-world transitions, such as a SOC Analyst moving to a Threat Intelligence role.
- Experience-based insights: Practical advice from seasoned professionals about overcoming challenges in each role.
Current Market Demand Information of a SOC Analyst Job
Understanding market trends is essential for aligning career goals with industry needs.
Market Trends:
High Demand for SOC Analysts Job:
The rise in cyber threats, such as ransomware and phishing attacks, has made SOC Analysts indispensable for organizations. Their role in protecting sensitive data and preventing breaches ensures their continuous demand across industries.
Growing interest in remote positions:
As companies adopt flexible work policies, the demand for remote SOC Analysts has surged. This shift allows professionals to work from anywhere while monitoring security systems and responding to incidents in real-time.
Strong correlation with SIEM tool searches:
SIEM tools like Splunk and QRadar are critical for monitoring and analyzing security data. Employers highly value candidates skilled in these platforms, as they enhance threat detection and incident management capabilities.
Important Elements:
- Current industry statistics: SOC Analysts are among the top in-demand roles in cybersecurity.
- Clear, actionable advice: Focus on emerging trends like AI in cybersecurity to stay ahead.
Tips for Success of a SOC Analyst Job
After years in the field, here are my top tips for succeeding as a SOC Analyst:
- Build a Home Lab
Set up virtual machines: Virtual machines let you create fake computer systems for practice. They’re like playgrounds where you can make mistakes safely.
Practice with security tools: Use tools like Wireshark (to see how data travels on a network) and Splunk (to spot patterns that might indicate a cyberattack).
Simulate attacks and detection: Pretend to be a hacker using programs like Metasploit to learn how attacks work and how to stop them.
- Stay Updated
Follow security blogs and news: Websites like “Krebs on Security” share the latest cybersecurity stories, so you know what hackers are up to.
Join professional communities: Groups like “(ISC)²” and “SANS Institute” can help you connect with experts and learn new skills.
Attend conferences when possible: Events like DEF CON are great places to learn about cool new tech and meet other cybersecurity fans.
- Develop Soft Skills
Practice clear communication: Learn how to explain tech stuff in simple ways, so everyone can understand your ideas.
Learn to work in teams: Teamwork matters when solving cyber problems because everyone has different skills to share.
Develop time management skills: Use tools like checklists or apps to stay on top of your tasks and avoid stress.
- Network with Others
Join LinkedIn groups: Find groups about cybersecurity on LinkedIn to connect with professionals and get advice.
Participate in local meetups: Go to events in your area to meet people who work in cybersecurity.
Engage in online forums: Join Reddit’s r/cybersecurity or Stack Exchange to ask questions and share what you’ve learned.
Conclusion
Now that you have a comprehensive understanding of the SOC Analyst job path, you’re better equipped to start your journey in cybersecurity.
Remember, every expert SOC Analyst started exactly where you are now.
Focus on building a strong foundation in security fundamentals, gain hands-on experience through labs and projects, and continuously update your skills.
The cybersecurity field is constantly evolving, and that’s what makes it so exciting!
Ready to take your first step toward becoming a SOC Analyst?
Check out our detailed guide on SOC Fundamentals: Mastering Tools, Roles, and Practices to start building your technical toolkit.
Stay secure!