Could a port scan attacks be silently probing your network for vulnerabilities right now?
Yes, it probably is. Port scan attacks happen thousands of times daily as hackers look for weak spots in computer networks.
In this analysis, we’ll look at a real example from LetsDefend to show you how these port scans work.
Using tools like Wireshark and Brim, we’ll walk through four key questions that help spot these hidden attacks.
Whether you’re new to cybersecurity or just curious, we’ll show you how security teams find and study these suspicious scans to protect their networks.
Check out our related guide: “Malicious Traffic: 9 Unbelievable Web Analysis Challenges
Join us as we explore step-by-step how to detect and analyze port scan activity using tools like Wireshark and Brim.
What Is A Port Scan Attack
Let me break down port scan attacks in a way that makes sense. Picture your computer like a house; the ports are all the doors and windows.
Now imagine someone walking around, checking which doors and windows are unlocked—that’s basically what a port scan is.
Here’s the deal: Port scanning isn’t always a bad thing.
Sometimes, it’s like double-checking your house to ensure everything’s secure. But when someone else does it without your permission? That’s when it starts to feel suspicious and not okay.
How Does a Port Scan Work?
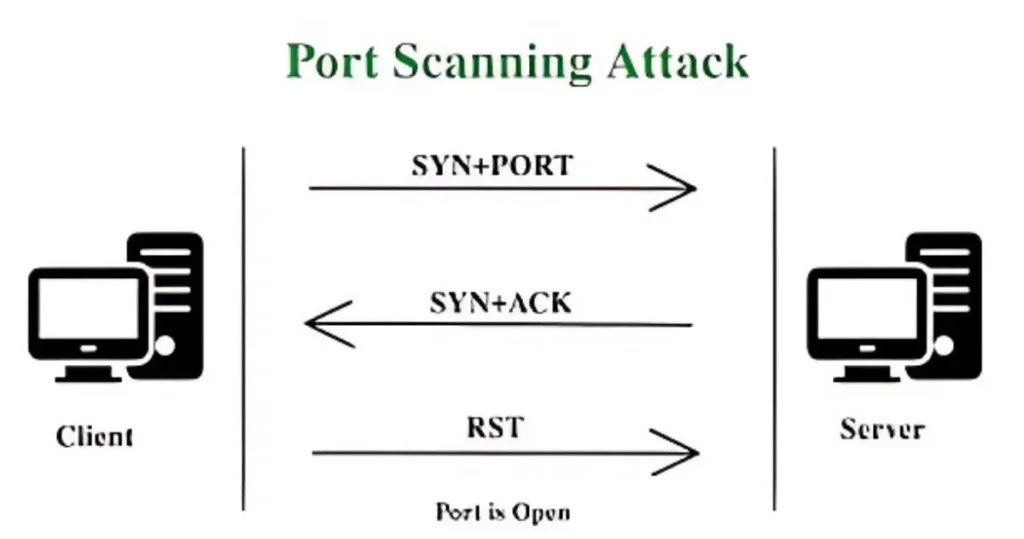
A port scan attacks involve an attacker sending small “probes” or “pings” to various ports on a target computer to determine their status.
These ports can be classified as open, closed, or filtered, based on the response received from the target server.
When an attacker initiates a port scan, they act as the client and send a SYN packet to a specific port on the target server.
This SYN packet is essentially a request to initiate a connection, asking the server, “Are you available to communicate on this port?”
The server’s response depends on the state of the port:
- Port Open: If the port is open, the server responds with a SYN+ACK packet, indicating that it is available and ready to establish a connection. However, instead of completing the handshake with an ACK packet, the attacker often sends an RST (reset packet) to terminate the connection immediately. This allows the attacker to identify open ports without engaging in a full session.
- Port Closed: If the port is closed, the server responds with an RST packet. This response signifies that the port is unavailable for communication.
- Port Filtered: If the port is filtered, the server either does not respond at all or the response is blocked by a firewall. This lack of response indicates that the port’s status is obscured, making it harder for the attacker to determine its state
Imagine a port on a computer like a door. An open port is like saying, “Hey, come on in!” to anyone passing by.
A closed port, on the other hand, firmly says, “No, not today.”
But a filtered port is sneakier—it doesn’t say anything, kind of like ignoring someone knocking on the door.
Once, while learning about networks, I made a beginner’s mistake and left an open port wide open during testing.
This is risky because an open port sends a “ready to connect” message (called SYN+ACK) to anyone asking, which could invite trouble, especially if it’s tied to a weak or outdated program.
After learning this lesson, I now always check all ports and settings carefully.
This habit keeps the computer safe by closing or filtering ports that aren’t needed.
Using firewalls also helps by acting like a guard, letting in only the right connections.
One key tool hackers use is port scanning.
They test doors (ports) by sending a special series of messages, like a handshake, to see which doors are open, closed, or filtered.
Knowing how this works helps in building stronger defenses for your network!
Types of Port Scan Attacks Technique
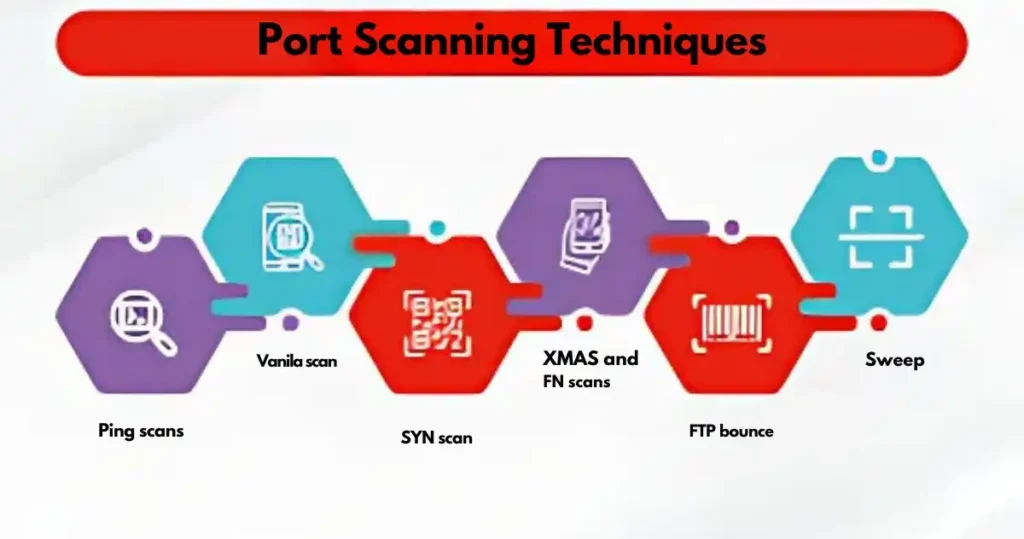
Port scan attacks are like testing different doors on a building to see which ones are open or unlocked.
Hackers use various methods to explore these “doors” (ports) on a network.
Ping scans are a basic approach, similar to ringing a doorbell to see who answers.
Hackers send a “ping” (ICMP echo request) to multiple devices to check which ones reply, indicating they are active and reachable.
This method is often used to identify potential targets quickly.
The vanilla scan is a thorough but noisy technique, like knocking on every single door in a building to see which ones open.
It involves trying to complete a full connection on every port, making it easy to detect but highly comprehensive.
On the other hand, the SYN scan is a faster and stealthier approach, where the attacker knocks briefly (sending a SYN packet) to see if the port responds without completing the handshake.
This method is efficient and often harder for security systems to detect.
For even more stealth, hackers may use XMAS scans and FIN scans, which are designed to bypass traditional defenses.
The XMAS scan sends packets with all TCP flags turned on, while the FIN scan sends a “finished” packet to test if a port is open without starting a conversation.
These methods probe the system quietly, looking for vulnerabilities without drawing much attention.
Similarly, the FTP bounce attack uses an unsecured FTP server as a middleman to scan other devices.
This allows attackers to hide their real IP addresses, making it more difficult to trace their activities.
Finally, the sweep scan involves sending the same request to multiple devices in a network, much like checking all the houses on a street to see which ones are occupied.
It’s a broad approach that maps active devices and identifies potential entry points.
Understanding these types of port scan attacks is essential for protecting networks.
Using firewalls, intrusion detection systems, and regular monitoring helps block unwanted scans and safeguard against potential threats.
Why Are Port Scan Attacks Dangerous?
Here’s the deal: port scan attacks are like someone sneaking around your house to see which doors are unlocked. They’re not breaking in yet but planning their next move. If an attacker spots an open port, they could figure out a way to use it to their advantage.
I remember feeling super annoyed when I noticed an unauthorized scan on my network. I thought, “Hey, what’s going on here? That’s my network!” But I quickly realized the best move was to stay calm and fix the problem instead of freaking out.
Here’s a simple tip: treat every open port like a potential risk. If you’re not using it, close it. Trust me, spending a few minutes now can save you a lot of trouble later.
Legitimate Uses of Port Scanning
Not all port scan attacks are bad.
Sometimes, scanning is like checking if your “house” doors are locked and secure.
Security experts and network administrators use it to protect networks and ensure everything is safe.
Once, I spent hours scanning to figure out why a service wasn’t working.
The problem turned out to be a blocked port.
Scanning tools are super helpful when you’re responsible for keeping things running smoothly.
Here’s a tip: Scanning your own network is fine, but never scan someone else’s without permission.
How to Protect Against Port Scan Attacks
Stopping port scan attacks is all about protecting your system.
Use a firewall to block scans that shouldn’t happen and close any ports you don’t need.
I learned this lesson the hard way.
I once thought my firewall was set up perfectly but left a big gap without realizing it.
Since then, I’ve made it a habit to double-check all my settings.
It’s also important to keep your software up to date.
Old programs can have weaknesses that attackers can use to their advantage.
Don’t give them a chance, alright?
Port Scan Attacks Challenge on Wireshark
What is the IP address scanning the environment?
During the research on port scan attacks, I analyzed the port scan PCAP file provided in Wireshark to identify the IP address scanning the environment.
I began by examining the packets captured in the file, specifically focusing on SYN packets, which are often the first step in a port scan.
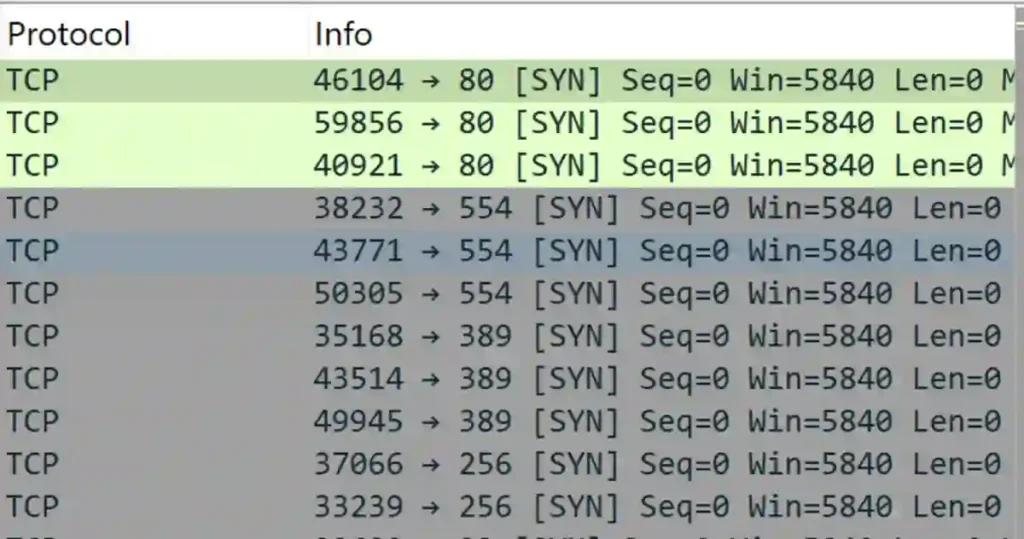
Using the filter tcp.flags.syn == 1 && tcp.flags.ack == 0, I isolated all connection attempts within the PCAP file.
From this filtered data, I noticed repeated SYN packets originating from a single IP address, 10.42.42.253, targeting multiple destinations.
To confirm this activity as a potential port scan attack, I used additional filters such as tcp.port == 80 for website traffic and tcp.port == 389 for directory services.
tcp.flags.syn == 1 && tcp.flags.ack == 0 && tcp.port == 80
I also combined these filters with tcp.flags.syn == 1 to narrow down the results and ensure I was accurately identifying scanning behavior.
tcp.flags.syn == 1 && (tcp.flags.ack == 0 && tcp.port == 80)
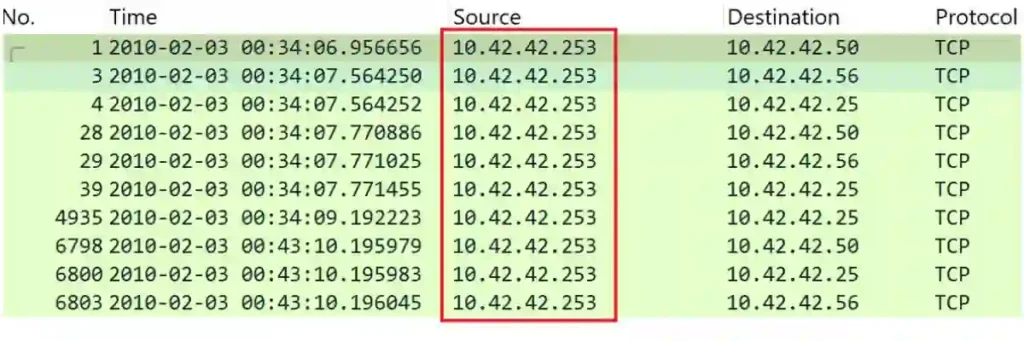
The repetitive and systematic nature of the packets originating from 10.42.42.253 indicated that this IP address was actively scanning the environment.
By saving and further analyzing the filtered packets, I confirmed that this IP was attempting to identify open ports on multiple devices, a classic behavior associated with port scan attacks.
This analysis demonstrated how examining SYN packets and their sources can effectively pinpoint the IP address responsible for scanning a network.
The IP address identified as scanning the environment in this case was 10.42.42.253.
This version focuses directly on answering the question while clearly explaining the steps you took to identify the scanning IP address.
Another way to do this is by filtering with ICMP then you can see the IP that is scanning the environment which is the most with the highest packet.
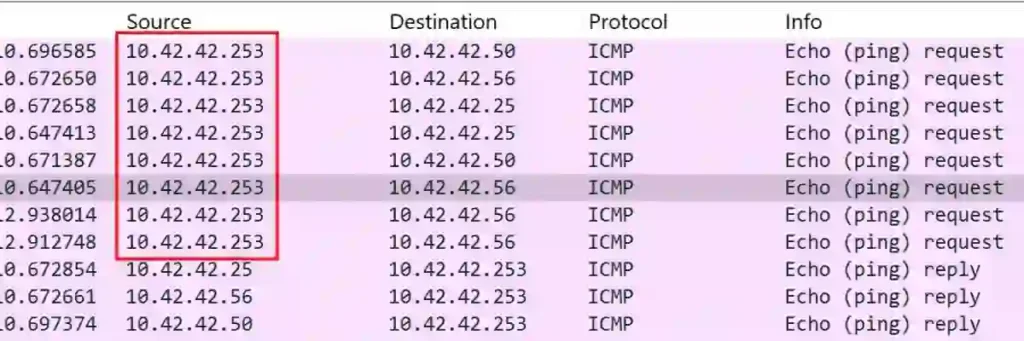
What is the IP address found as a result of the scan?
At first, I wasn’t completely sure what the question was asking because there were three other IP addresses involved: 10.42.42.25, 10.42.42.50, and 10.42.42.56.
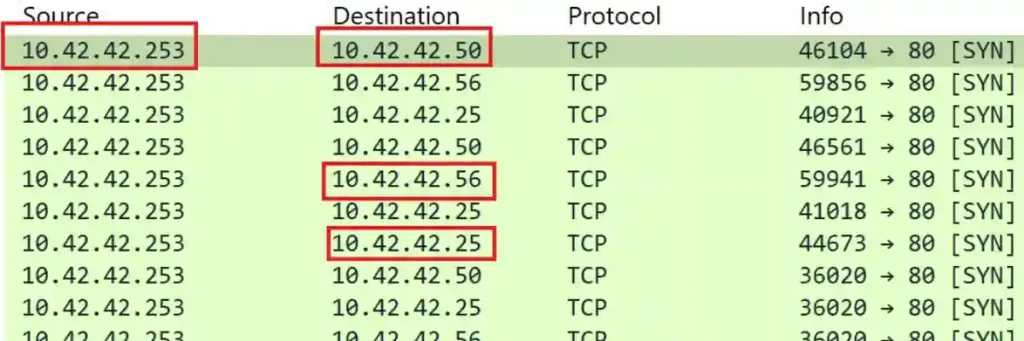
I guessed that the question referred to identifying a successful TCP connection from the scanning IP address.
I began by carefully examining the logs in the PCAP file and noticed successful TCP connections on ports 135 (RPC) and 139 (NetBIOS) for the IP address 10.42.42.50.
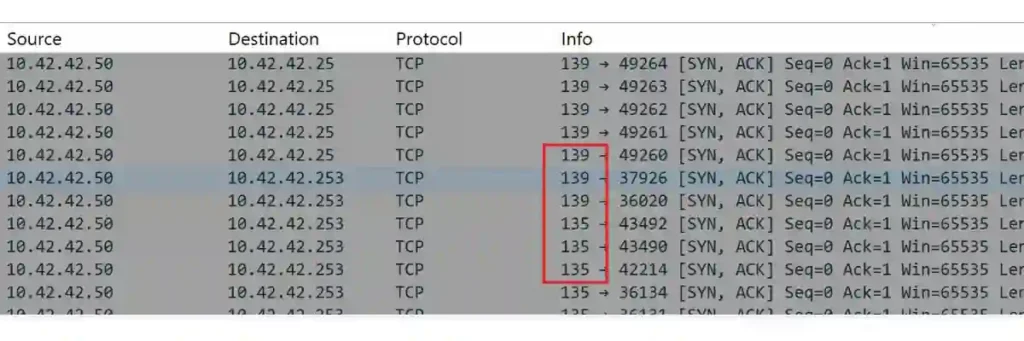
To investigate further, I applied the Wireshark filter ip.addr == 10.42.42.253 && tcp.flags.ack == 1 && tcp.flags.syn == 0 && tcp.flags.reset == 0 to isolate packets with the ACK flag set.
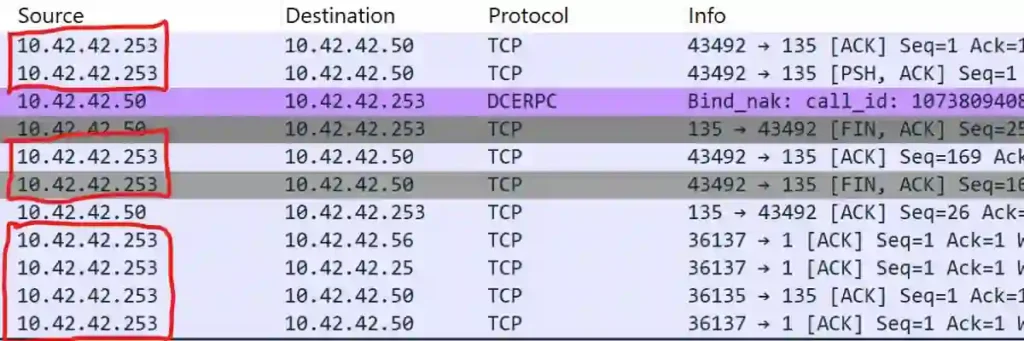
After analyzing the filtered packets, I discovered that 10.42.42.50 was the only IP address that received an ACK packet from the scanning IP, 10.42.42.253.
Based on this evidence, I concluded that the correct answer to the question is 10.42.42.50.
This analysis demonstrated how the use of packet filters and careful examination of logs in Wireshark can help identify the target of a port scan attack.
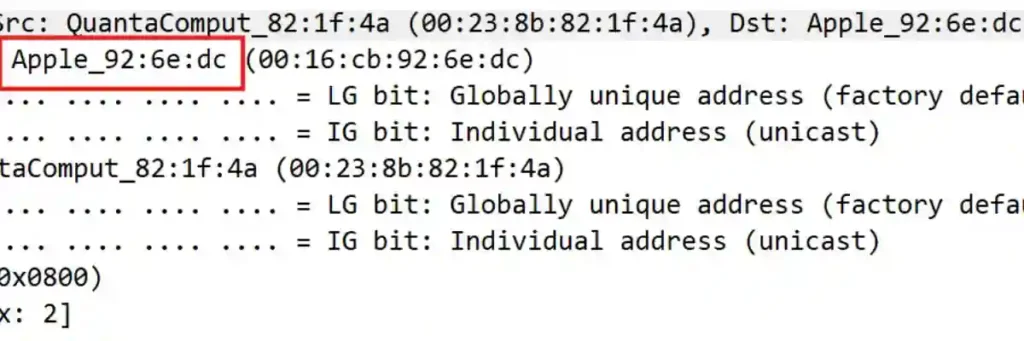
What is the MAC address of the Apple system it finds?
I started by examining the network packets captured in the PCAP file.
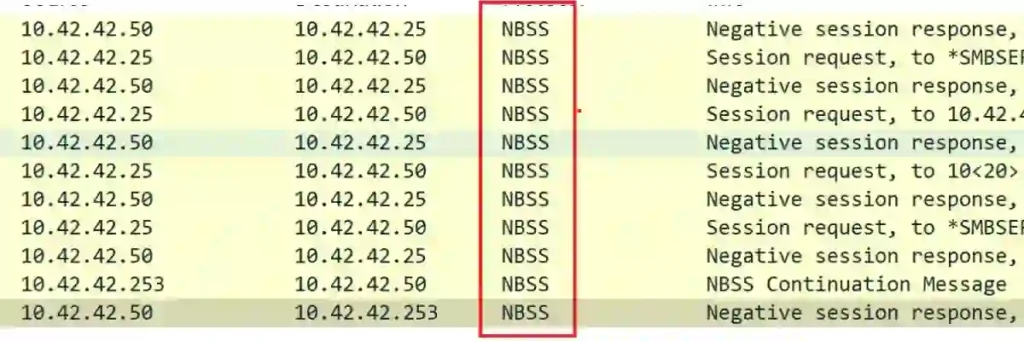
To narrow my focus, I applied the nbss filter in Wireshark to isolate NetBIOS Session Service packets.
These packets were easy to spot because they were sent to the broadcast address of the LAN.
By inspecting the packet details in the NetBIOS Session Service section, I located the NetBIOS name of the device.
Next, I examined the Ethernet II protocol section of the same packet.
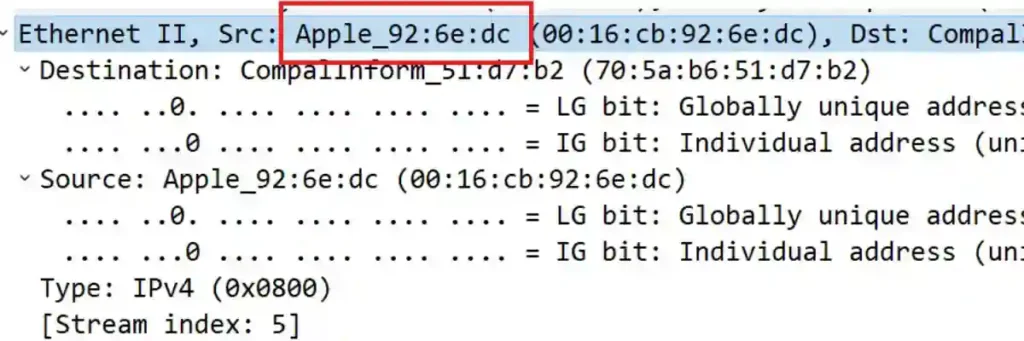
In this section, I identified the source labeled as “Apple_92:6e:dc”.
To confirm this was the correct device, I matched the source label with the MAC address displayed next to the NetBIOS name.
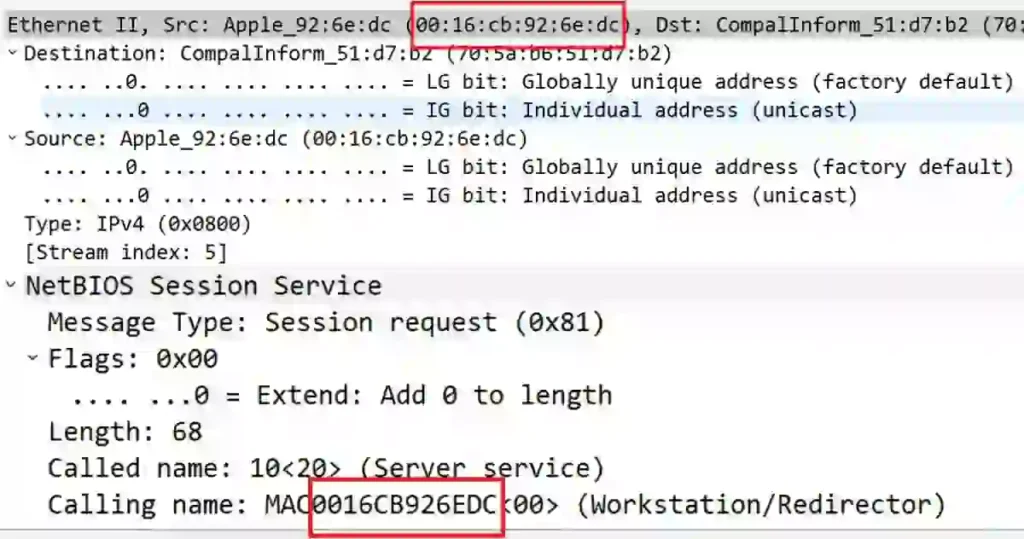
Through this process, I was able to determine the MAC address of the Apple system in question.
This analysis demonstrated how tools like Wireshark can help identify devices and their activity during port scan attacks, highlighting the importance of examining specific packet details for accurate results.
The MAC address of the Apple system I found is 00:16:cb:92:6e:dc.
What is the IP address of the detected Windows system?
I started by analyzing the packets in the file and identified four key IP addresses: 10.42.42.25, 10.42.42.50, 10.42.42.56, and 10.42.42.253.
To focus on the scanning activity, I applied the filter ip.src == 10.42.42.253 to view all traffic originating from the suspected scanning IP.
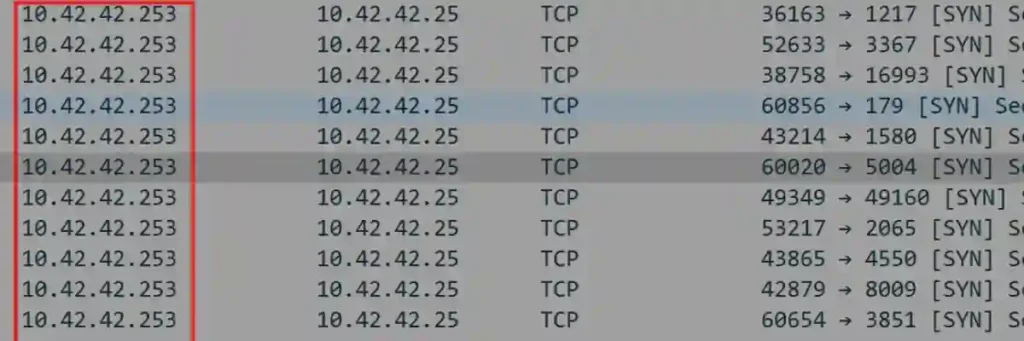
This analysis revealed that IP address 10.42.42.253 was sending repeated SYN packets, confirming it as the device conducting the port scan attack.
Using Wireshark’s features, I identified that IP address 10.42.42.25 belonged to an Apple device based on its MAC address and NetBIOS name.
Next, I applied the filter tcp.flags.ack == 1 && ip.src == 10.42.42.253 to locate successful TCP connections initiated by the scanning IP.
This revealed that IP address 10.42.42.50 was the only device that completed a TCP-Connect handshake with the scanner.
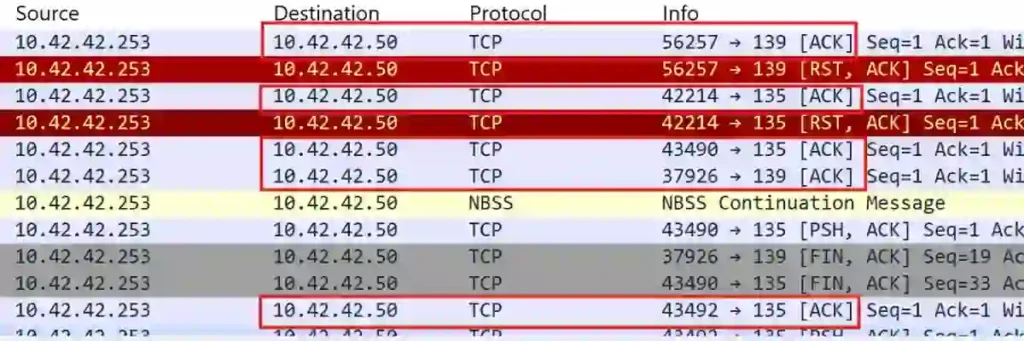
The successful handshake indicated that 10.42.42.50 was the detected Windows system responding to the port scan attack.
Through this process, I confirmed that the detected Windows system in the environment had the IP address 10.42.42.50.
FAQs on Port Scan Attacks and Effective Incident Response
Why Do I Keep Getting Port Scan Attacks?
Port scan attacks occur because attackers are searching for vulnerabilities in your system. Open ports can serve as entry points for unauthorized access or exploitation. Common reasons include:
- Exposed Services: Services running on open ports may be visible to attackers.
- Lack of Firewall Rules: An improperly configured firewall may leave ports unnecessarily exposed.
- No Regular Updates: Outdated software may have vulnerabilities attackers target.
- Being on Public Networks: Devices on public or unsecured networks are more likely to be scanned.
To reduce these attacks, ensure you use firewalls, close unnecessary ports, and monitor network activity regularly.
You Are Working as a Network Administrator, and You Want to Conduct Simulated Attacks on a Network to Determine Its Weaknesses. To Do So, You Want to Check for Open Ports So That You Can Remote in Using That Port and Craft an Attack. Which of the Following Software Will You Use to Scan for Open Ports in This Scenario?
The best tools for scanning open ports in such a scenario are:
- Nmap (Network Mapper):
- A popular tool for port scanning, identifying open ports, and mapping a network’s security posture.
- Zenmap:
- A graphical user interface for Nmap, making it easier to visualize scan results.
- Masscan:
- Known for its speed, it can scan a vast range of IP addresses and ports.
- Angry IP Scanner:
- Lightweight and user-friendly, useful for smaller-scale port scanning tasks.
These tools can help you identify open ports and simulate attacks for vulnerability assessments.
How to Stop Port Scan Attacks?
To stop or mitigate the impact of port scan attacks, follow these steps:
- Use a Firewall:
- Configure firewalls to block unused ports and restrict access to critical services.
- Enable Intrusion Detection/Prevention Systems (IDS/IPS):
- These systems can detect port scans and block the attacker’s IP address.
- Close Unnecessary Ports:
- Regularly audit your network to close ports that are not in use.
- Implement Rate Limiting:
- Restrict the number of connection attempts from a single IP address within a specific time frame.
- Use Port Knocking:
- This technique keeps ports closed until a specific sequence of connection attempts is made, adding an extra layer of security.
- Monitor Network Traffic:
- Use tools like Wireshark or SolarWinds to detect unusual patterns that may indicate scanning activity.
By implementing these strategies, you can significantly reduce the risk posed by port scan attacks.
What is port scan and DoS protection?
Port scan and DoS protection refers to security measures that detect and block unauthorized port scans and prevent denial-of-service attacks from overwhelming systems.
What is the purpose of a port scanner?
A port scanner is a tool used to identify open, closed, or filtered ports on a network, helping attackers or security teams assess network vulnerabilities.
Is port scanning an active or passive attack?
Port scanning is considered an active attack because it involves sending packets to network ports to gather information, which can trigger alerts.
What does it mean when a port scan is blocked?
When a port scan is blocked, it indicates that a firewall or intrusion detection system has detected and prevented the scan, safeguarding the network.
Can firewalls block port scanning?
Yes, firewalls can block port scanning by filtering traffic, using intrusion detection systems, and enforcing strict access controls.
Why is port scanning attractive to attackers?
Port scanning helps attackers find vulnerable ports and services, making it easier to exploit weaknesses and gain unauthorized access.
How many types of port scanning are there?
There are several types of port scanning, including TCP connect scan, SYN scan, UDP scan, FIN scan, XMAS scan, and NULL scan, each serving different purposes.
What is the difference between port scan and port sweep?
A port scan targets multiple ports on a single host, while a port sweep scans the same port across multiple hosts to identify devices running a specific service.
Conclusion
Port Scan Attacks can seem tricky, but with the right tools and tips, you can find and stop them before they cause harm.
By learning how to analyze traffic and recognize scan patterns, you can keep your network safe and secure.
Don’t wait to take action—start using these tips to protect your system today.
Empower yourself with these simple strategies and make your network stronger right away.
I remember the first time I found a port scan on my network—it was frustrating, but taking quick action fixed everything.
Check out: “SOC Fundamentals: Mastering Tools, Roles, and Practices.
