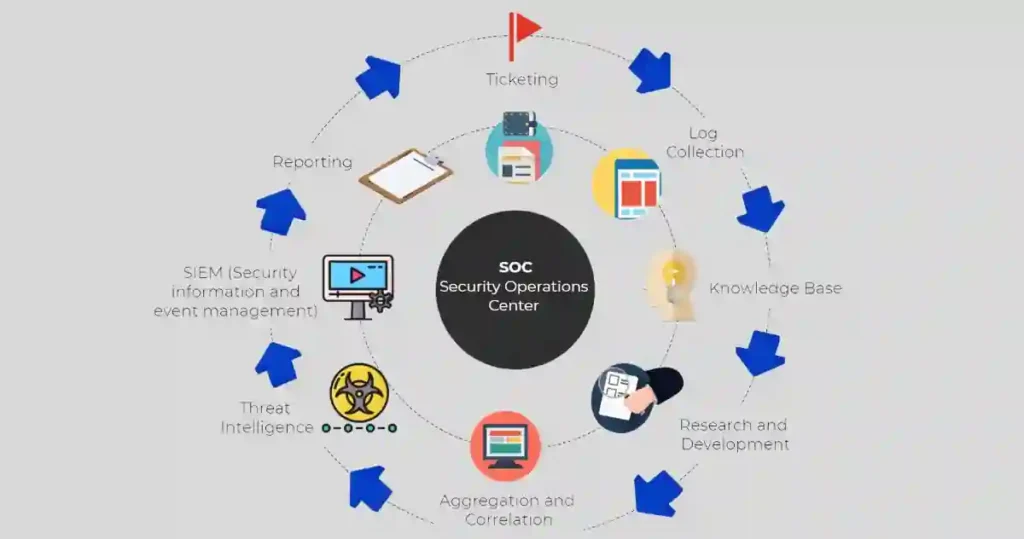
Have you ever wondered why mastering SOC Fundamentals is crucial for protecting organizations from cyber threats?
It’s because they provide the foundation for effective threat detection, response, and prevention in a Security Operations Center (SOC).
Without understanding these basics, businesses are left vulnerable to breaches and advanced attacks.
SOC analysts rely on tools like SIEM, EDR, and Log Management to safeguard systems, making their role indispensable in today’s digital landscape.
This guide will walk you through the essentials of SOC, practical tips, and best practices to get started.
See also: “SOC Essentials: Tools and Techniques for Beginners.”
Let’s dive in!
What is a SOC?
Think of a Security Operations Center (SOC) as a superhero’s headquarters.
It’s the command center where security teams unite to monitor and protect organizations from cyber threats every second of every day.
The primary mission of a Security Operations Center?
Detect, analyze, and respond to security incidents before they can cause significant damage or disruption.
At the heart of SOC Fundamentals, you’ll find three core components: teamwork, advanced technology, and streamlined processes working in perfect synchronization.
In my early days, I believed a SOC was all about flashy screens and sophisticated dashboards, much like what you see in action-packed movies.
But here’s the reality:
An effective SOC isn’t just about fancy gadgets; it’s about well-trained analysts, cutting-edge cybersecurity tools, and efficient workflows.
To better understand SOCs, let’s break down the core fundamentals into a table:
| SOC Component | Role in Cybersecurity |
| Teamwork | Collaboration among analysts to detect threats quickly |
| Technology | Use of advanced tools like SIEM (Security Information and Event Management) for data analysis |
| Processes | Predefined steps for handling incidents effectively |
Did you know that, according to a 2023 Cybersecurity Ventures report, global organizations faced an average of 2,200 cyberattacks per day?
This makes the role of SoCs evens more important in today’s digital world.
Some experts also refer to the SOC as the nerve center of an organization’s cybersecurity defenses, emphasizing its role in maintaining business continuity.
Understanding SOC basics isn’t just for IT professionals; even students can appreciate how these centers work behind the scenes to protect the systems we rely on daily.
By exploring SOC principles, you’ll see how teamwork, tools, and procedures create a shield against cyber threats, ensuring data security and organizational resilience.
For a deeper dive into how SOCs operate, visit Cybersecurity Basics: SOC Explained.
Types of SOC Models: A Beginner’s Guide to SOC Fundamentals
When it comes to Security Operations Center (SOC) models, there isn’t one solution that works for everyone. Organizations tailor their SOC structures based on their budget, security needs, and available expertise. Here’s a breakdown of the different types:
1. In-House SOC
- Definition: Think of this as building a cybersecurity fortress within your organization.
- Key Features:
- The organization hires and trains its cybersecurity analysts.
- Offers full control over security operations.
- Pros and Cons:
- Advantages: High-security customization and control.
- Disadvantages: High costs for hiring, training, and maintaining the team.
- Example: A large bank with a robust budget may invest in an in-house SOC to guard against financial cyber threats.
- Key Takeaway: Without consistent investment, an in-house cyber defense team may face challenges in keeping up with evolving threats.
2. Virtual SOC
- Definition: Ideal for companies with remote teams, a virtual Security Operations Center functions without a physical office.
- Key Features:
- Teams collaborate entirely online using secure platforms.
- Focuses on incident monitoring and threat management through cloud tools.
- Pros and Cons:
- Advantages: Cost-effective and location-flexible.
- Disadvantages: Requires flawless communication and coordination to function effectively.
- Example: A tech startup with limited resources might rely on a virtual SOC to oversee its cybersecurity.
- Key Takeaway: A remote SOC team can be effective but demands strong leadership and organization.
3. Co-Managed SOC
- Definition: A hybrid approach combining internal resources with a Managed Security Service Provider (MSSP).
- Key Features:
- Internal teams collaborate with external experts to handle threats.
- Responsibility is shared, providing both flexibility and scalability.
- Pros and Cons:
- Advantages: Access to external expertise while retaining some control.
- Disadvantages: Clear communication is important to stop any confusion about roles.
- Example: Mid-sized companies often use this model to strengthen their security posture without committing to a full in-house setup.
- Key Takeaway: With co-managed SOCs, effective communication between teams is the backbone of success.
4. Command SOC
- Definition: The “big boss” of all SOC models, overseeing multiple regional Security Operations Centers.
- Key Features:
- Acts as a central command hub for managing smaller SOC units.
- Typically used by industries like telecommunications and defense.
- Pros and Cons:
- Advantages: Centralized control allows for coordinated, large-scale cybersecurity operations.
- Disadvantages: Requires significant resources and highly skilled professionals to manage.
- Example: A defense agency might employ a command SOC to monitor national-level cybersecurity threats.
- Key Takeaway: Command SOCs are designed for large-scale operations, ensuring smooth coordination across regional centers.
SOC Fundamentals in Summary
| SOC Model | Key Features | Best For |
| In-House SOC | Full control, tailored security | Large organizations with big budgets |
| Virtual SOC | Remote collaboration, cost-efficient | Startups and remote-friendly teams |
| Co-Managed SOC | Shared responsibility with MSSPs | Mid-sized businesses |
| Command SOC | Centralized control over multiple centers | Telecom and defense agencies |
Source for Further Reading
To learn more about SOC structures and strategies, check out this guide on SOC best practices.
People, Process, and Technology in SOC Fundamentals
Building a Security Operations Center (SOC) isn’t just about hiring skilled professionals or acquiring advanced tools.
It’s about harmonizing people, processes, and technology into an effective and cohesive unit.
People
SOC teams are the frontline defenders against cybersecurity threats.
They are responsible for identifying, analyzing, and mitigating potential risks to an organization.
To excel, they must continuously update their knowledge about new attack vectors, emerging security frameworks, and innovative defense techniques.
Tip: Keep learning constantly—cybersecurity changes daily, and your skills should grow with it.
| Key Traits of SOC Personnel | Why They Matter |
| Analytical Thinking | To quickly assess and respond to threats. |
| Communication Skills | To report incidents clearly and collaborate effectively. |
| Technical Expertise | To configure tools and understand threat landscapes. |
Processes
Establishing robust SOC fundamentals requires adhering to industry-recognized standards like NIST Cybersecurity Framework or PCI DSS.
Processes ensure consistency, efficiency, and compliance across all SOC operations.
Skipping process documentation, as I learned early on, leads to chaos—it’s nearly impossible to troubleshoot effectively without clear guidelines.
| Standard | Focus Area |
| NIST | Risk Management and Response |
Pro Tip: Documenting processes helps streamline operations and enables smooth onboarding of new team members.
Technology
Selecting the right technology is a critical aspect of SOC operations.
From penetration testing tools that identify vulnerabilities to SIEM (Security Information and Event Management) solutions that monitor and analyze logs, each tool plays a vital role.
However, the “best” tool isn’t necessarily the most expensive; it’s about finding what aligns with your organization’s needs and budget.
| Type of Technology | Purpose | Examples |
| SIEM Tools | Log Analysis and Threat Detection | Splunk, QRadar |
| Penetration Testing | Vulnerability Identification | Nessus, Metasploit |
- Pro Tip: Focus on tools that integrate seamlessly with your processes and enable your team to work efficiently.
Key Roles in SOC Fundamentals
A Security Operations Center (SOC) works like a smoothly running machine, where every team member plays an important part in its success. Here’s an overview of the key roles that help a SOC function effectively:
1. SOC Analyst (Levels 1, 2, 3)
The SOC analyst is the first line of defense in any cybersecurity framework.
- Primary Tasks: Classify alerts, investigate potential threats, and recommend responses.
- Level 1 Analysts focus on monitoring and triaging alerts.
- Level 2 Analysts dig deeper into incidents to validate threats.
- Level 3 Analysts handle advanced investigations and incident remediation strategies.
This role is foundational to maintaining the integrity of SOC operations and a key part of SOC Fundamentals.
2. Incident Responder
Think of the incident responder as a firefighter, but for cyber threats.
- Responsibilities: Detect and respond swiftly to security breaches.
- Skills Required: Strong problem-solving abilities and a calm approach during crises.
Incident responders are essential to ensuring that SOC processes run smoothly, embodying the proactive measures emphasized in SOC Essentials.
3. Threat Hunter
The threat hunter proactively seeks out vulnerabilities before attackers exploit them.
- Tasks: Investigate systems for hidden threats, uncover weak points, and strengthen defenses.
- Ideal for: Those who enjoy detective-like investigative work.
Threat hunting is a crucial component of SOC Operations, ensuring that potential risks are identified and mitigated before they escalate.
4. Security Engineer
The security engineer ensures that the SOC infrastructure is maintained and continuously improved.
- Role in SOC Fundamentals: Implement security measures, manage software updates, and enhance tools used in operations.
- Contribution: Their work ensures the SOC is prepared to handle emerging cyber threats effectively.
This often overlooked role forms the backbone of a well-functioning SOC.
5. SOC Manager
A SOC manager combines technical expertise with leadership skills.
- Duties: Manage the team, budget, and overall strategy of the SOC.
- Key Responsibilities: Coordinate efforts among team members and ensure alignment with organizational goals.
This role emphasizes strategic planning within the broader scope of SOC Structures, balancing hands-on technical work with administrative oversight.
Table: SOC Roles and Responsibilities
| Role | Primary Responsibilities | Key Skills Required |
| SOC Analyst | Monitor alerts, investigate threats, and suggest responses. | Analytical thinking, communication |
| Incident Responder | Detect and respond to breaches. | Problem-solving, crisis management |
| Threat Hunter | Proactively identify and address vulnerabilities. | Investigative skills, creativity |
| Security Engineer | Maintain and improve SOC tools and infrastructure. | Technical expertise, innovation |
| SOC Manager | Lead the team, budget, and strategy. | Leadership, strategic thinking |
Essential Tools for SOC Analysts
SIEM (Security Information and Event Management)
When I first tried using a SIEM, it felt like magic—alerts would pop up whenever something suspicious happened.
But here’s the truth: SIEMs are only as effective as the rules you configure. If you set up poor rules, you’ll get poor results.
For instance, I often use Wazuh, a well-known SIEM tool that works by using carefully set-up rules. It also lets you create custom rules to effectively find and respond to threats.
What is SIEM?
- A system that logs and analyzes events across your network.
- Alerts you to suspicious patterns, like failed logins or mass file deletions.
Popular SIEM Solutions:
- Splunk
- IBM QRadar
- Microsoft Sentinel
Pro Tip: SIEM alerts can sometimes be false positives. Learn to spot these and tweak rules to save time.
Log Management
Logs are like breadcrumbs—they show where things went wrong.
In one situation, I tracked malware activity back to a single entry in the proxy log.
Without log management, I would have had to search through thousands of files by hand.
Why It’s Important:
- Centralizes logs from different systems like firewalls, servers, and applications.
- Speeds up investigations.
EDR (Endpoint Detection and Response)
This tool is your best friend for investigating endpoint devices like laptops or servers.
Why You’ll Love It:
- Tracks File Changes: EDR solutions are designed to monitor file activities on endpoint devices.
This includes tracking modifications, deletions, and new file creations to identify potential threats. - Monitors Network Connections: It keeps a close watch on the network activities of endpoint devices.
By analyzing incoming and outgoing connections, it can detect unusual patterns indicating an attack. - Analyze Running Processes: EDR tools examine processes running on endpoints, identifying malicious or unauthorized processes.
- Device Isolation for Malware Containment: When a threat is detected, EDR enables the isolation of infected devices.
This helps stop malware from spreading across your network, protecting other systems.
The Role of EDR in SOC Fundamentals
EDR is an important part of SOC Basics (Security Operations Center Fundamentals). It helps detect and respond to security threats on individual devices.
- Endpoint Monitoring: EDR solutions are a key part of a SOC. They closely monitor activities on devices to catch any harmful actions that might otherwise be missed.
- Incident Response: EDR tools help SOC teams respond quickly, stopping threats and reducing the damage caused by security breaches.
Synonyms for “SOC Fundamentals” in Context
- Security Operations Center Essentials: EDR tools are a key part of these essentials, enabling effective monitoring and response.
- SOC Basics: Understanding tools like EDR is foundational in mastering SOC basics.
Example Table: EDR Features and Benefits
| Feature | Benefit |
| File Change Tracking | Identifies suspicious file activities |
| Network Connection Analysis | Detects anomalous network behavior |
| Process Monitoring | Identifies malicious processes |
| Device Isolation | Prevents malware spread |
Supporting Statistics
- Organizations with EDR implemented detect threats 40% faster compared to those without (Source: Cybersecurity Ventures).
Integrating EDR into SOC Fundamentals improves your skills in protecting endpoint devices and keeping the network secure.
Avoiding Common SOC Mistakes: A Guide to SOC Fundamentals
Understanding SOC Fundamentals is key to avoiding costly errors in managing security operations centers. Below are some common mistakes and tips to overcome them effectively:
1. Over-reliance on VirusTotal
While VirusTotal is a powerful tool, over-reliance on it can be a mistake.
Not all malware is detected by VirusTotal.
Always corroborate findings with other threat intelligence tools and malware analysis fundamentals to ensure comprehensive detection.
2. Hasty Sandbox Analysis
Malware doesn’t always reveal its true behavior immediately.
If sandbox analysis is done too quickly, you might miss key indicators of compromise.
To master threat detection principles, allow malware sufficient time to execute fully in a controlled environment.
3. Incomplete Log Analysis
Looking only at flagged devices can leave you blind to related threats.
Logs from associated systems often reveal important clues about lateral movement or coordinated attacks.
This is a basic practice in log analysis methodologies, which emphasize cross-system examination for deeper insights.
4. Ignoring Context
Alerts can seem minor when viewed in isolation.
However, every alert could be part of a larger, coordinated attack.
Understanding the context of alerts in SOC operations is essential to connect the dots and mitigate larger threats.
Frequently Asked Questions (FAQs)
1. When you close an alert, which channel can you access it from?
Once an alert is closed, it is stored in the “Closed Cases” channel of your SOC system.
This feature of incident management frameworks provides a historical reference for investigations.
2. What source IP address entered the URL ‘https://github.com/apache/flink/compare‘?
To identify the source IP address:
- Access your Log Management system.
- Look for log entries associated with the URL.
- Note the corresponding source IP.
This is a fundamental step in network traffic analysis basics.
3. What type of log has a destination port number of 52567 and a source IP address of 8.8.8.8?
Logs with this information are typically firewall logs or network traffic logs.
These logs capture communication details between source and destination, a key focus of firewall log fundamentals.
4. What is the hostname of the device where the “nmap” file with a hash value of “83e0cfc95de1153d405e839e53d408f5” is executed?
Use an EDR tool to search for the hash value across hosts.
The endpoint detection principles of the tool will identify the hostname associated with the file execution.
5. A “Ps1.hta” file was executed on a device with the hostname “Roberto.” What is the complete CMD command?
To find the full CMD command:
- Open the Process List in your EDR solution.
- Search for “Ps1.hta” on the device “Roberto.”
- Review the logs for the complete CMD command.
This process aligns with threat analysis strategies for process monitoring.
6. What is the data source of the “e1def6e8ab4b5bcb650037df234e2973” hash on the Threat Intel page?
Navigate to the Threat Intelligence Feed page and locate the hash.
The data source may be malware analysis, sandbox reports, or other feeds.
This is a practical example of threat intelligence basics.
7. Which type of SOC team does not have its facility and often works remotely in different locations?
A Virtual SOC operates without a permanent physical location.
This type of SOC, part of remote SOC management practices, offers flexibility and cost-efficiency for organizations.
Summary Table: Key SOC Mistakes and Their Solutions
| Common Mistake | Solution | Related SOC Fundamental |
| Over-reliance on VirusTotal | Use additional tools and corroborate findings. | Malware Analysis Fundamentals |
| Hasty Sandbox Analysis | Allow sufficient time for malware execution. | Threat Detection Principles |
| Incomplete Log Analysis | Analyze logs from all related systems. | Log Analysis Methodologies |
| Ignoring Context | Evaluate alerts within the broader attack framework. | Contextual Alert Analysis |
Sources:
- SOC Best Practices
- Threat Intelligence Fundamentals
Conclusion
Now that you’ve explored the SOC Fundamentals, you’re ready to take on cybersecurity challenges.
Mastering tools like SIEM, Log Management, and EDR is your first step toward becoming an indispensable part of any SOC team.
Remember, being a great SOC analyst isn’t about tools, but critical thinking and staying curious.
Ready to dive deeper?
Check out our article, “Advanced SOC Techniques: Level Up Your Skills Today!”